From /48 to /128 — A No‑Tears Guide to IPv6 Subnets, Routing & SLAAC

Why this guide exists
Back in 2014 I earned Hurricane Electric’s Sage badge (and a great T‑shirt that took a good ten years till it died the washing machine death). Eleven years later I still meet engineers and plenty of Jane & Joe Bloggs who recoil at an IPv6 prefix like 2a02:8012:bc57::/48.

This article is the conversation I wish I’d had back then. It’s built as a Q‑and‑A, because every section grew out of an actual head‑scratcher raised while deploying the network below.

Before we dig in lets confirm the IPv6 Address of this website is:
2a05:d01c:65b:7100:f50:5bf:250c:dc5f
https://articles.akadata.ltd is much nicer to read don't you think?
Lab topology referenced throughout
ISP (Zen) -- PPPoE --> ppp0 (route)
|
+-- eth0 ⇢ Wi‑Fi hotspot
+-- eth1 ⇢ "homer" workstation
+-- eth3 ⇢ VM switch / servers
The ISP delegates one /48; we slice and dice it for LANs, point‑to‑points and DHCP pools.
Those DHCP Pools are much simpler than you may expect, simply install DHCPCD on Linux, use the example configuration and adapt to the number of interfaces you have and thats it the /48 gets given as soon as it is requested
# General Settings /etc/dhcpcd.conf
controlgroup wheel
noipv4ll
noipv6rs
persistent
vendorclassid
require dhcp_server_identifier
option domain_name_servers, domain_name, domain_search
option classless_static_routes
option interface_mtu
option host_name
option ntp_servers
slaac hwaddr # Using MAC-based EUI-64 for stable IPv6 addresses
# Fallback DNS
static domain_name_servers=2a02:8010:1::212:23:3:100 2001:4860:4860::8888 2001:4860:4860::8844 8.8.8.8 1.1.1.1
denyinterfaces eth2 # Don't touch eth2 parent interface
denyinterfaces eth2.911 # Don't touch PPPoE VLAN interface directly
interface ppp0
ipv6rs # Enable Router Solicitation just here
ia_na 0 # Request ND prefix for ppp0 (WAN address)
ia_pd 2/::48 eth0/0/64 eth1/1/64 eth3/3/64
# UPDATE: 26/07/2025 - The ia_pd 2::48 is the answer to stable /48 allocation and assign /64 subnets from /48 delegation
The proof below, yes they are live IPv6 addresses Yes you can ping them, No SSH is not available to the world, nftables our friend and a little honeypot to be discussed later, if the hackers will hack we let them be trapped in a playground
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 state UNKNOWN qlen 1000
inet6 ::1/128 scope host proto kernel_lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 2a02:8012:bc57::1/64 scope global dynamic noprefixroute
valid_lft 81113sec preferred_lft 81113sec
inet6 fe80::e654:e8ff:feaa:df36/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 2a02:8012:bc57:1::1/64 scope global dynamic noprefixroute
valid_lft 81113sec preferred_lft 81113sec
inet6 fe80::c2a1:c3ff:fea3:f111/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 fe80::6e92:bfff:fe67:bc8c/64 scope link
valid_lft forever preferred_lft forever
5: eth3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 2a02:8012:bc57:3::1/64 scope global dynamic noprefixroute
valid_lft 81113sec preferred_lft 81113sec
inet6 fe80::6e92:bfff:fe67:bc8d/64 scope link
valid_lft forever preferred_lft forever
6: eth2.911@eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 fe80::6e92:bfff:fe67:bc8c/64 scope link
valid_lft forever preferred_lft forever
7: ppp0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1280 state UNKNOWN qlen 3
inet6 2a02:8011:d017:cba8::1/64 scope global dynamic mngtmpaddr noprefixroute
valid_lft 2591466sec preferred_lft 604266sec
inet6 fe80::1 peer fe80::827f:f8ff:fe74:b8d7/128 scope link nodad
valid_lft forever preferred_lft foreverWe can browse IPv6 websites, connect from AWS where this site is hosted back to any of the addresses above and some of the internal addresses too.
Bonus: radvd.conf — Announcing routes to clients
To enable SLAAC and propagate DNS search domains, we pair the DHCPv6 configuration with radvd — the Router Advertisement Daemon. Each interface advertises its IPv6 prefix, DNS server, and local search domain.
With this, Radvd ensures:
- Each interface advertises its /64 prefix to clients.
- Clients know the router is on-link and can self-assign addresses using SLAAC.
- DNS servers (RDNSS) and search domains (DNSSL) are passed along automatically.
- RA intervals (
MaxRtrAdvInterval) are kept reasonable to balance network responsiveness with traffic efficiency.
interface eth0 {
AdvSendAdvert on;
MaxRtrAdvInterval 30;
prefix 2a02:8012:bc57:1::/64 {
AdvOnLink on;
AdvAutonomous on;
};
RDNSS 2a02:8012:bc57:1::1 {
AdvRDNSSLifetime 600;
};
DNSSL zerodns.co.uk {
AdvDNSSLLifetime 600;
};
};
interface eth1 {
AdvSendAdvert on;
MaxRtrAdvInterval 30;
prefix 2a02:8012:bc57:2::/64 {
AdvOnLink on;
AdvAutonomous on;
};
RDNSS 2a02:8012:bc57:2::1 {
AdvRDNSSLifetime 3600;
};
DNSSL akadata.ltd {
AdvDNSSLLifetime 3600;
};
};
interface eth3 {
AdvSendAdvert on;
MaxRtrAdvInterval 30;
prefix 2a02:8012:bc57:3::/64 {
AdvOnLink on;
AdvAutonomous on;
};
RDNSS 2a02:8012:bc57:3::1 {
AdvRDNSSLifetime 600;
};
DNSSL breathtechnology.co.uk {
AdvDNSSLLifetime 600;
};
};This configuration enables IPv6-only clients to:
- Learn their address via SLAAC,
- Discover the on-link prefix and default gateway,
- Receive IPv6 DNS info (via
RDNSSandDNSSL) — without needing DHCPv6.
💡radvdis essential if DHCPv6 is omitted or if clients (like Android) ignore DHCPv6 entirely. Always test withrdisc6andping6.
🛰️ How Radvd Works with dhcpcd/SLAAC
After configuring dhcpcd.conf to request only the global /48 prefix and disable auto-SLAAC, you'll need Radvd to advertise individual /64 subnets on your LAN interfaces. This is crucial because Radvd:
- Signals each LAN segment's default gateway.
- Posts Router Advertisements (RA) that include both the on-link (
A) flag for address configuration and the DNS RA (RDNSS/DNSSL) options for name resolution settings. - Ensures that connected clients on
eth0,eth1, andeth3can configure IPv6 addresses automatically (SLAAC) and learn the local DNS servers and search domains.
1 · “What does a /48 really give me?”
A /48 gives you 65 536 /64s because:
2^(64‑48) = 2^16 = 65 536
Every /64 is the canonical SLAAC‑capable LAN and holds 18.4 quintillion host addresses (2^64).
Example allocation2a02:8012:bc57::/48
Valid /64s include:
2a02:8012:bc57:0000::/642a02:8012:bc57:0001::/64…2a02:8012:bc57:ffff::/64
2 · “How do I carve space between /48 and /64?”
| CIDR | # Subnets from /48 | /64s inside each | Hosts per subnet |
|---|---|---|---|
| /49 | 2 | 32 768 | 2^79 ≈ 6e23 |
| /50 | 4 | 16 384 | 2^78 |
| /52 | 16 | 4 096 | 2^76 |
| /56 | 256 | 256 | 2^72 |
| /60 | 4 096 | 16 | 2^68 |
| /64 | 65 536 | 1 | 2^64 = 18 446 744 073 709 551 616 |
Rule‑of‑thumb: subnet for organisational clarity, never to “save addresses”.
3 · “When do /126, /112 or /128 make sense?”
| Prefix | Typical use‑case | Address count |
|---|---|---|
| /126 | Router‑to‑router link | 4 (like IPv4 /30) |
| /127 | Modern alternative to /31 – one addr each side | 2 |
| /112 | DHCP pool or hotspot (think IPv4 /24) | 65 536 |
| /128 | Loopback or a single VIP | 1 |
Captive‑portal example
Pool: 2a02:8012:bc57:3:abcd:abcd::1‑fffe/112
4 · “What’s actually between the colons?”
An address = 8×16‑bit hex words:
2a02:8012:bc57:1:abcd:abcd:1234:5678
│<—— netid ——>│ │<—— host id ——>│
- Zero‑compression
::subs consecutive zeros:…:1::1→…:1:0:0:0:0:0:1 - Interface IDs can be static, privacy‑random, or EUI‑64‑derived.
5 · “Why do I see fe80:: everywhere?”
fe80::/10 = link‑local. Used exclusively for:
- Router Advertisements (RA)
- Neighbor Discovery (ND)
- Next‑hop in local routing tables
Not routed beyond one hop.
6 · “What are RA & SLAAC and why should I care?”
Routers multicast ICMPv6 RA every ~30 s announcing:
- The on‑link prefix (/64)
- Default‑gateway flag
Hosts combine that prefix with their Interface ID → SLAAC address. No RA = no automatic IPv6.
7 · “Show me a real routing table.”
ip -6 route
2a02:8012:bc57::/64 dev eth0 proto dhcp
2a02:8012:bc57:1::/64 dev eth1 proto dhcp
2a02:8012:bc57:3::/64 dev eth3 proto dhcp
unreachable 2a02:8012:bc57::/48 dev lo proto dhcp # safety catch‑all
fe80::1 dev ppp0 # ISP LLA
…
default dev ppp0
unreachable /48 prevents leaks between overlapping prefixes.
8 · “Is IPv6 subnetting opposite to IPv4?”
Not opposite—just scaled:
- IPv4
/29(‑‑->) 6 hosts - IPv6
/126(‑‑->) 2 hosts
But for “normal” LANs IPv6 always uses/64regardless of user‑count.
9 · “Multi‑router? Multiple hops?”
- Advertise RA only toward clients.
- Use static routes or OSPFv3/BGP between routers.
- If you delegate sub‑prefixes with DHCPv6‑PD downstream, each downstream router advertises its own RA.
10 · Transition trick: decoding embedded IPv4
2002:c0a8:0001::/48 → c0a8:0001 = 192.168.0.1 (hex→dec per byte). Handy for 6to4, 4in6, etc.
☕ Humour Break — “IPv6 readiness tests” that aren’t”
I once disabled IPv4 to “prove” dual‑stack‑ness. Two famous IPv6 test sites promptly failed… because they had no AAAA records!
$ dig AAAA ipv6test.l.google.com +short # returns nothing
$ dig AAAA test-ipv6.com +short # also empty
Lesson: always dig your diagnostics before blaming the network. Even giants forget to walk their own talk, still adding IPv4 back at least test-ipv6.com worked
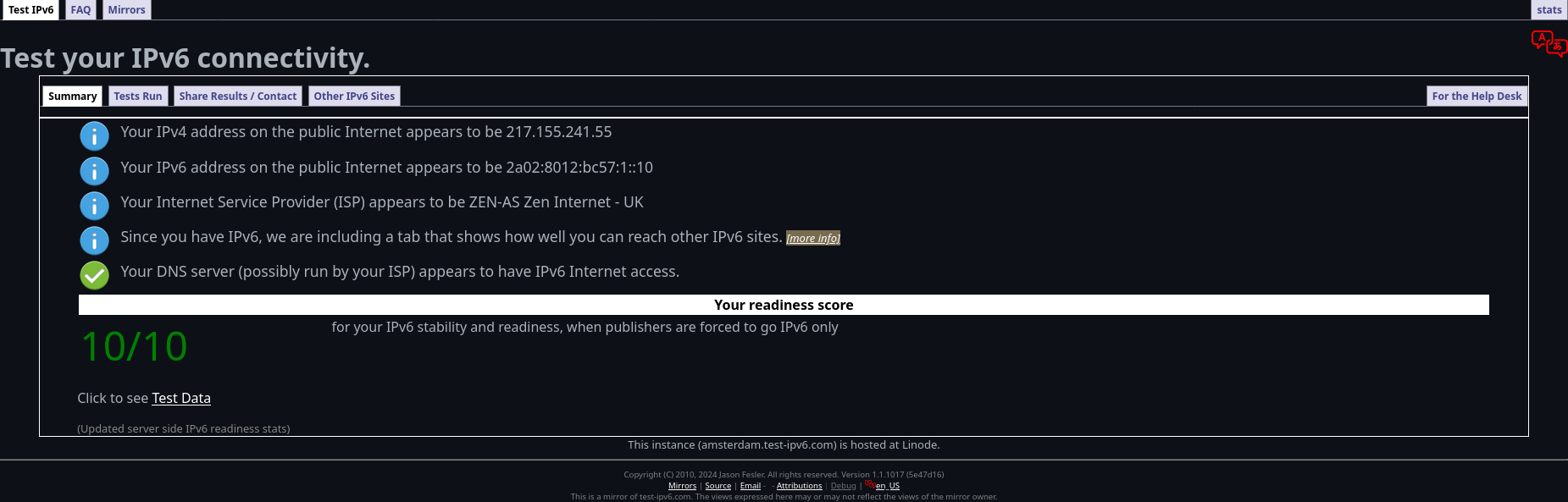
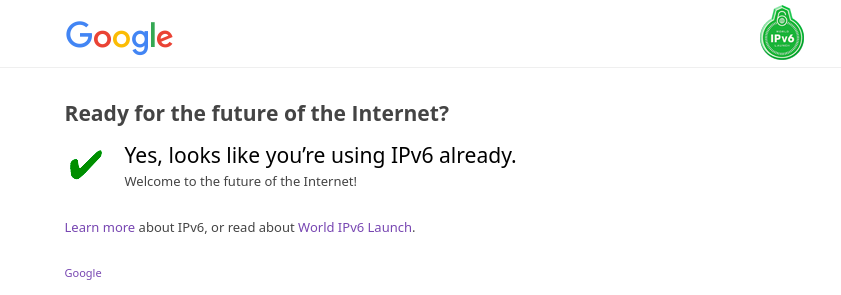
Also https://ipv6test.google.com/ did work however it also required the presence of IPv4 network address and that distinct lack of an IPv6 AAAA record for it's site a contradiction to the little green IPv6 logo we see on the website.
11 · Quick address‑space mental model
| /48 |----------- your kingdom -----------|
| /56 |-- Dept --| /56 |-- IoT --|
| /64 | Home WiFi |
/112 DHCP pool
Take‑aways
/64for every user‑facing LAN./112for big DHCP pools;/126for P2P.- RA is king for clients; routing protocols for routers.
- Use “unreachable /48” as a safety net.
- Test‑IPv6 sites might fail their own tests—don’t panic!
Next up: IPv6 firewalling with nftables—myths, must‑haves, and mistakes to dodge.
